It has been somewhat interesting to watch how security vulnerabilities have evolved over the past twenty years or so that I’ve been working with computers anyway. For the most part in the early days security exploits were pretty harmless. Maybe your company got hacked to leverage it’s bandwidth/disk space for pirated software or something like that.
The past several years though the rise in organized cyber crime and highly sophisticated attacks (even attacks from folks that some may consider friendly) is rather alarming. I do feel sorry for those in the security field, especially those at bigger organizations, whom by nature are bigger targets. They are (for the most part) fighting a war they simply cannot win. Sooner or later they will be breached, and one interesting stat I heard last year at a presentation given by the CTO of Trend Micro was that the average attacker has access to a network to 210 days before being detected.
Companies can spend millions to billions of dollars on equipment, training, and staffing to protect themselves but it’ll never be enough. I mean look no further than the NSA and Snowden? How much did he get away with again? The NSA admits they don’t even know.
I wish the company that sponsored the event had published a video of this CTO presentation as I thought it was the most interesting I had/seen heard in years. Here is another video from another event that he presented at, also quite good – though not as long as the presentation I saw.
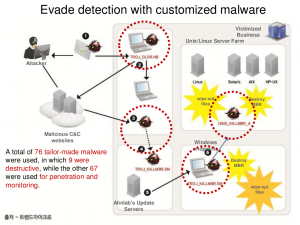
Some details on a highly sophisticated successful attack executed against Korean banks targeting multiple platforms
The slide above shows a very large scale attack which had more than seventy custom malware packages built for it!
The recent highly sophisticated attacks against Target and Neiman Marcus are of course just the recent high profile examples.
The security of SCADA systems has long been a problem as well.
Over 60,000 exposed control systems found online.
Researchers have found vulnerabilities in industrial control systems that they say grant full control of systems running energy, chemical and transportation systems.
Speaking of industrial control systems, going back to the Trend Micro presentation they mentioned how they purchased some similar equipment to do some testing with. Their first tests involved a water pressure control station connected to the internet and they just watched to see who tried to attack it. This was a real system (not connected to any water source or supporting anybody).
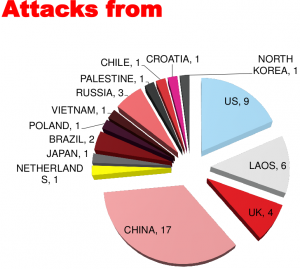
One of the interesting bits was he noted that although there were a large number of attacks from China most of them were simply probing for information, they were not destructive. I don’t remember who had the destructive attacks I want to say Laos and the U.S. but I could be wrong. He said since this test was so successful they were planning (perhaps already had) to purchase several more of these and place them around the world for monitoring.
I’ve never been too deep in security, I can count on one hand the number of times I’ve had to deal with a compromised system over the past 15 years(most recent one was a couple of months ago). Taking real basic security precautions protects you against a very large number of threats by default(with the most recent attack I dealt with I noted at least three best practices any of which would of prevented the attack from occurring, all of which would of had no impact to the system or application though none were in place), though at the end of the day your best defense against a targeted attack – is don’t be a target to begin with. Obviously that is impossible for big organizations.
The recent DDoS attacks against gaming companies I believe impacted the company I work for, not because we are a gaming company but because we share the same ISP. The ISP responded quite well to the attacks in my opinion and later wrote a letter to all customers describing the attacks – an NTP amplification attack that exceeded 100Gbps in volume, the largest attack they had ever seen. It’s the first DOS attack that has impacted stuff I operate that I’ve ever experienced to my knowledge.